Security and Compliance Overview
Relyt has adopted a range of advanced security technologies and measures to keep your accounts, data, and network connections secure. With multiple security compliance certifications under its belt, Relyt is committed to providing you with the highest standards of protection. These measures ensure that data stored on the Relyt platform is secure and meet the stringent data security compliance requirements of enterprises.
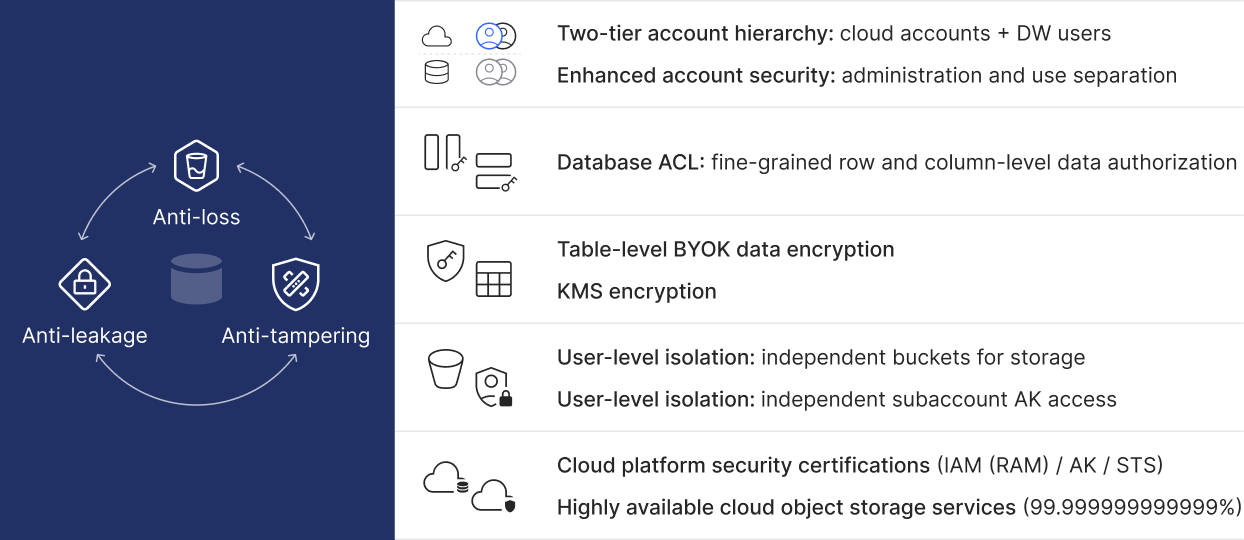
Account security
To ensure the highest level of data security, Relyt uses a "two-tier account" hierarchy and an "administration and use separation" strategy, combined with an invitation-only registration policy. This significantly enhances the security of your data and privacy.
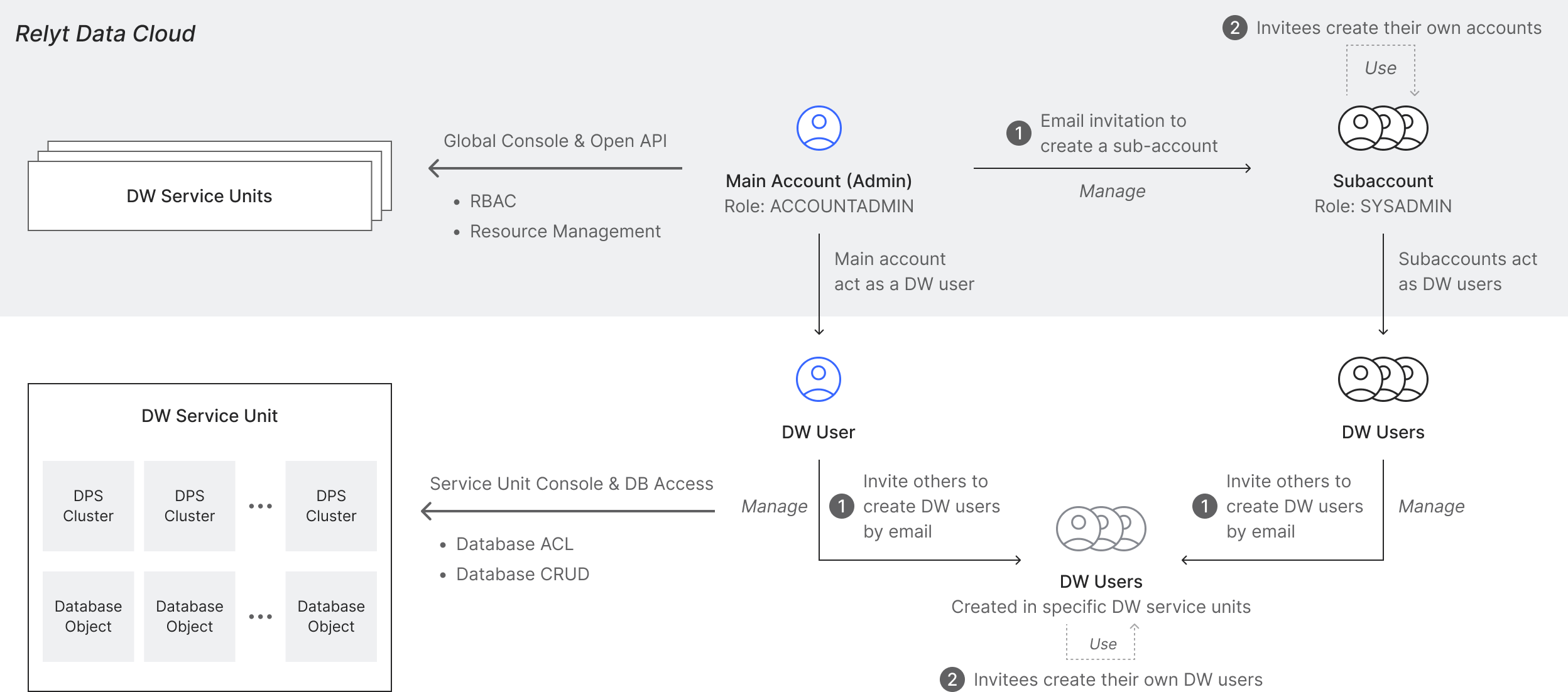
On Relyt, user accounts are divided into two tiers: cloud accounts (further divided into main accounts and subaccounts) and DW users. Cloud accounts are used for managing cloud accounts and DW service units on the global console, while DW users manage and operate database objects within DW service units. This physical separation of resource management from data operations achieves the "administration" and "use" separation, ensuring the security of data and systems.
Additionally, Relyt uses an invitation-only registration policy for creating subaccounts and DW users, ensuring that only invited individuals can create user accounts. Only the creators know the passwords, preventing data leaks and tampering, and thereby fully protecting your privacy.
For more information on cloud accounts and DW users, see Cloud Accounts and DW Users.
Data security
Data encryption
Relyt takes data security to the next level by supporting table-level encryption with Bring Your Own Key (BYOK) and allowing you to leverage your own cloud key management service (KMS) for encryption. This powerful combination ensures that you retain full control over your encryption keys, preventing unauthorized access. By putting the power of encryption in your hands, Relyt not only safeguards your data against potential breaches but also ensures compliance with stringent regulatory data security requirements. With Relyt, you can be confident that your data is protected by the most advanced and customizable security measures available, providing robust protection and meeting the highest standards of data security compliance.
Highly reliable object storage
Relyt leverages cutting-edge cloud object storage services to store your data, providing unmatched safety, reliability, and scalability. Currently, Relyt supports the following leading cloud providers' object storage services, each renowned for their superior performance and reliability:
-
Amazon S3: provides 99.99999999% data durability and 99.99% availability. Learn more
-
Alibaba Cloud OSS: provides 99.9999999999% data durability and 99.995% availability. Learn more
-
Tencent Cloud COS: provides 99.9999999999% data durability. Learn more
-
Kingsoft Cloud KS3: provides 99.999999999% data durability.
Data isolation
To ensure user data security, Relyt employs two robust isolation methods:
-
Independent buckets: Each user’s data is meticulously stored in separate buckets, providing ironclad user-level data isolation. This approach not only safeguards your data from unauthorized access but also streamlines data backup and recovery processes, ensuring that your data is always available and protected, even in the event of a disruption.
-
Independent subaccount AK access: Relyt assigns unique Access Keys (AK) to individual subaccounts, guaranteeing that sensitive data is only accessible to authorized personnel. This stringent access control mechanism fortifies data security, preventing unauthorized access and significantly reducing the risk of data breaches. By ensuring that only vetted individuals can access critical data, Relyt reinforces your data's integrity and confidentiality, providing you with peace of mind that your information is secure.
Database ACL
Relyt fully supports PostgreSQL protocol-based Access Control List (ACL) mechanisms, enabling row and column-level data authorization. With ACL, you can achieve fine-grained authorization at both the row and column levels, adhering to the principle of least privilege. This approach ensures data isolation between different DW users, significantly reducing the risk of data leakage.
For more information, see Object Privileges.
Network security
Relyt not only implements network access isolation between DW service units through architectural design but also enhances network security through configurable network policies and private links.
With network policies, you can precisely control which IP addresses are allowed to access specific DW service units, ensuring only authorized users can access your information. For more information, see Network Policies.
Additionally, private links allow you to establish secure, private connections between your VPCs deployed on other clouds and your DW service units, keeping your data traffic off the public internet. This comprehensive approach ensures robust protection against unauthorized access and potential security breaches. For more information, see Private Link.
Compliance certification
Relyt has achieved prestigious compliance certifications, including ISO 20000, ISO 27001, and GDPR. These certifications highlight our commitment to the highest standards of security and data protection. By meeting these rigorous requirements, Relyt ensures your data is secure and compliant with global standards. Trust Relyt to safeguard your operations and provide peace of mind, knowing your data is in expert hands.