Create a Private Link
Private Link enables you to create a secure connection between your Virtual Private Cloud (VPC) hosted on a third-party public cloud and your DW service unit, ensuring that your traffic between the VPC and the service unit remains isolated from public networks.
Private Link provides several significant benefits over public network-based access, including:
-
Superior security measures for controlling data access to database resources on Relyt.
-
Elimination of the need for route configuration to establish a secure connection, thereby streamlining the process of data access.
-
Compatibility with VPCs from leading cloud provider AWS, offering unrestricted location access and global reach.
Before you start
To create a private link, ensure the following:
-
The DW service unit and the VPC to connect must be deployed on the same region provided by the same cloud provider.
infoAt present, AWS is the only third-party cloud supported by Private Link.
-
You have obtained a Relyt cloud account with access permissions to the DW service unit.
For details about how to create a DW service unit, see Create a DW Service Unit.
-
You have obtained an AWS account with access permissions to the Amazon VPC.
Use the DW service unit console to create a private link
Step 1. Enable the endpoint service on Relyt
-
Sign in to the Relyt global console.
infoEnsure that you log in as
SYSTEMADMIN. If your current system role isACCOUNTADMIN, click the dropdown button next toACCOUNTADMINand switch the role toSYSTEMADMINin the drop-down list.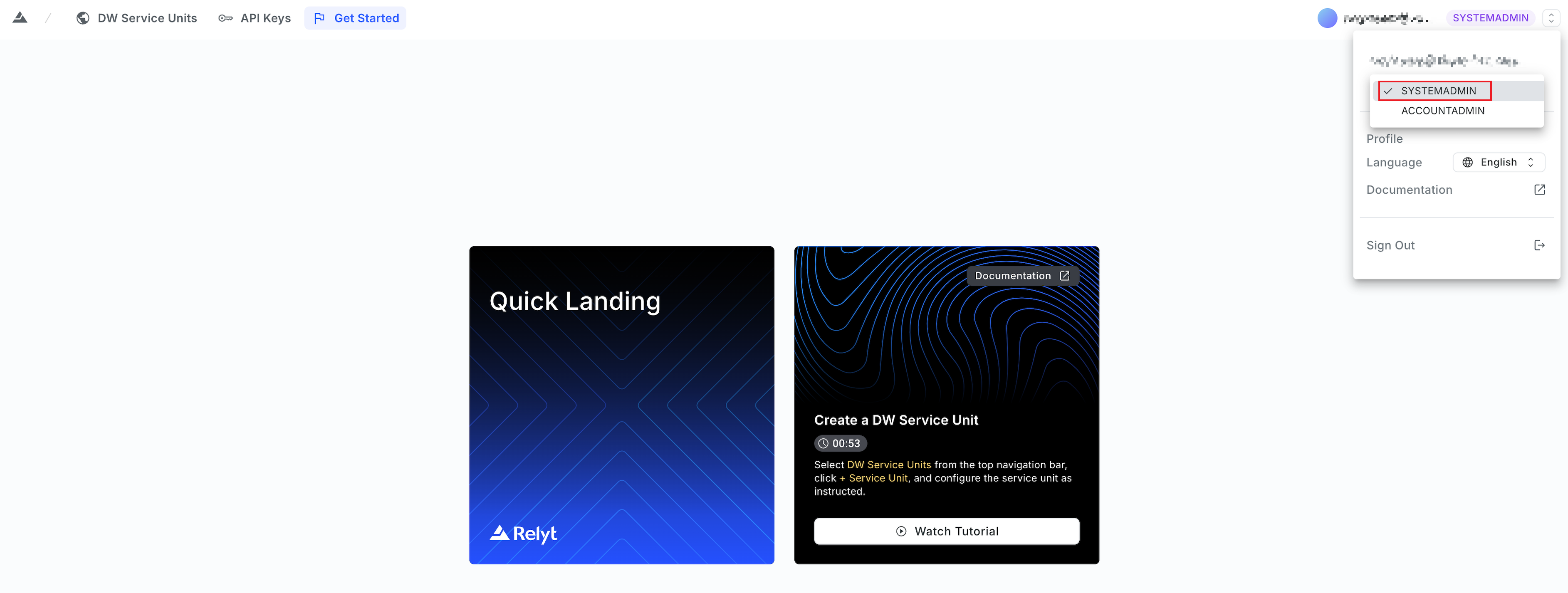
-
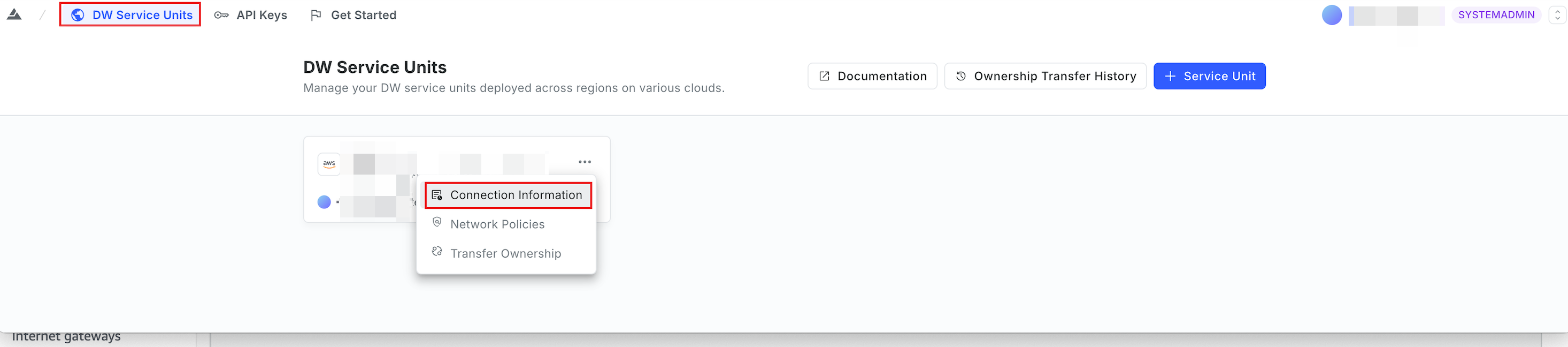
Select DW Service Units from the top navigation bar.
-
Hover over the upper-right corner of the target DW service unit card and select Connection Information from the drop-down list.
-
On the Connection Information page, select the target tab, and click Enable Endpoint Service in the Enable Your Endpoint Service section. The process may take a few minutes to complete, so please wait patiently.
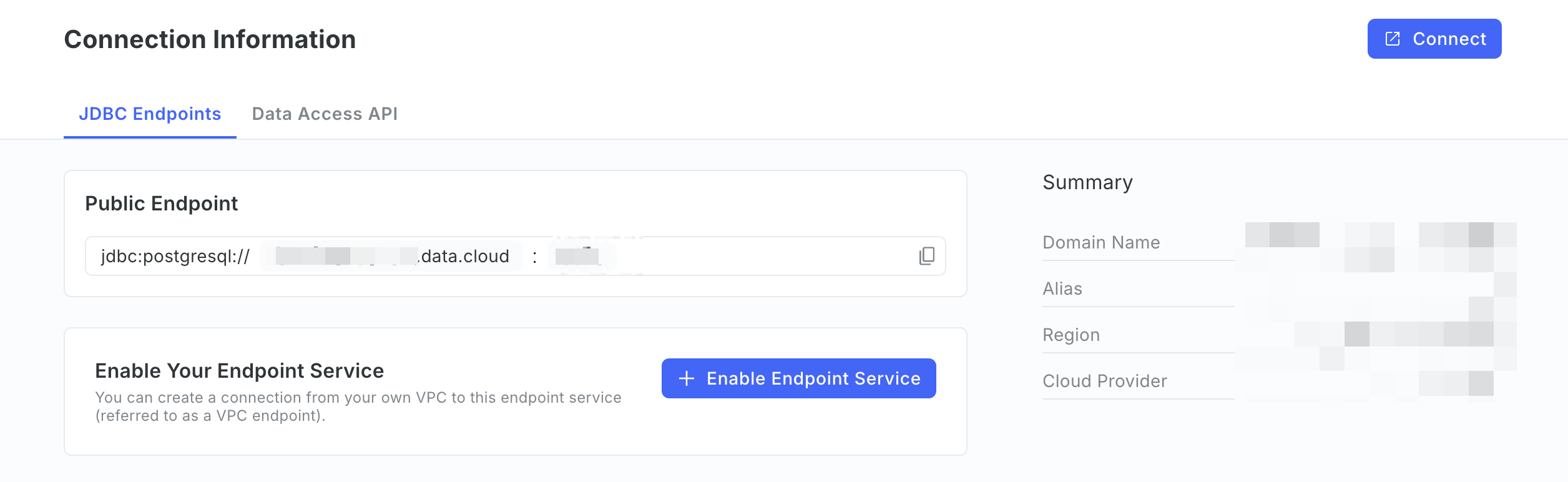
In this example, the JDBC Endpoints tab is selected to create a private link for JDBC access. To create one for Boto3 access, select the Data Access API tab instead.
-
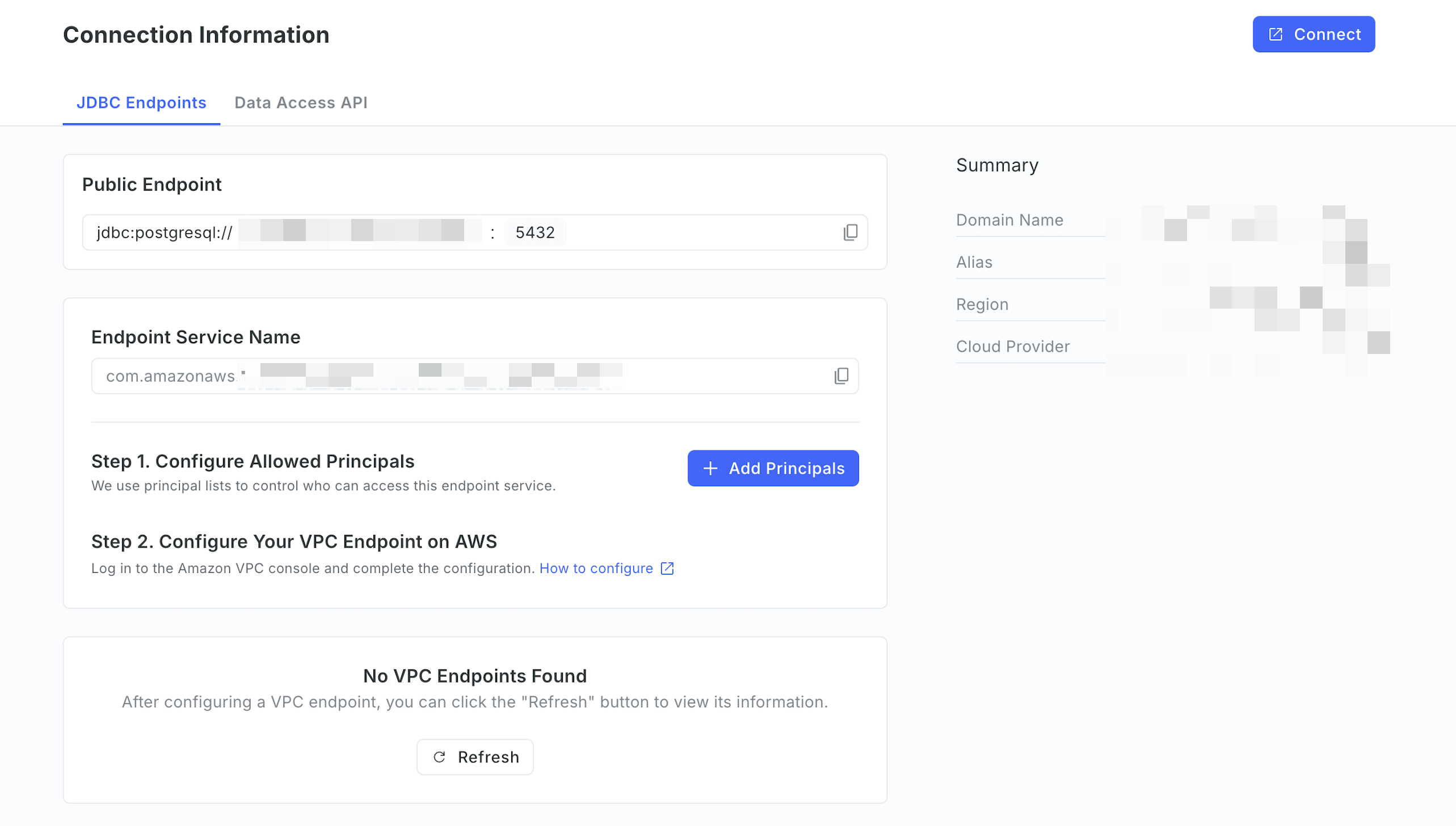
After enabled, click Add Principals.
 tip
tipIf the DW service unit is already connected to at least one VPC, you can simply click Edit in step 1 to modify the allowed principals. There's no need to enable the endpoint service again.
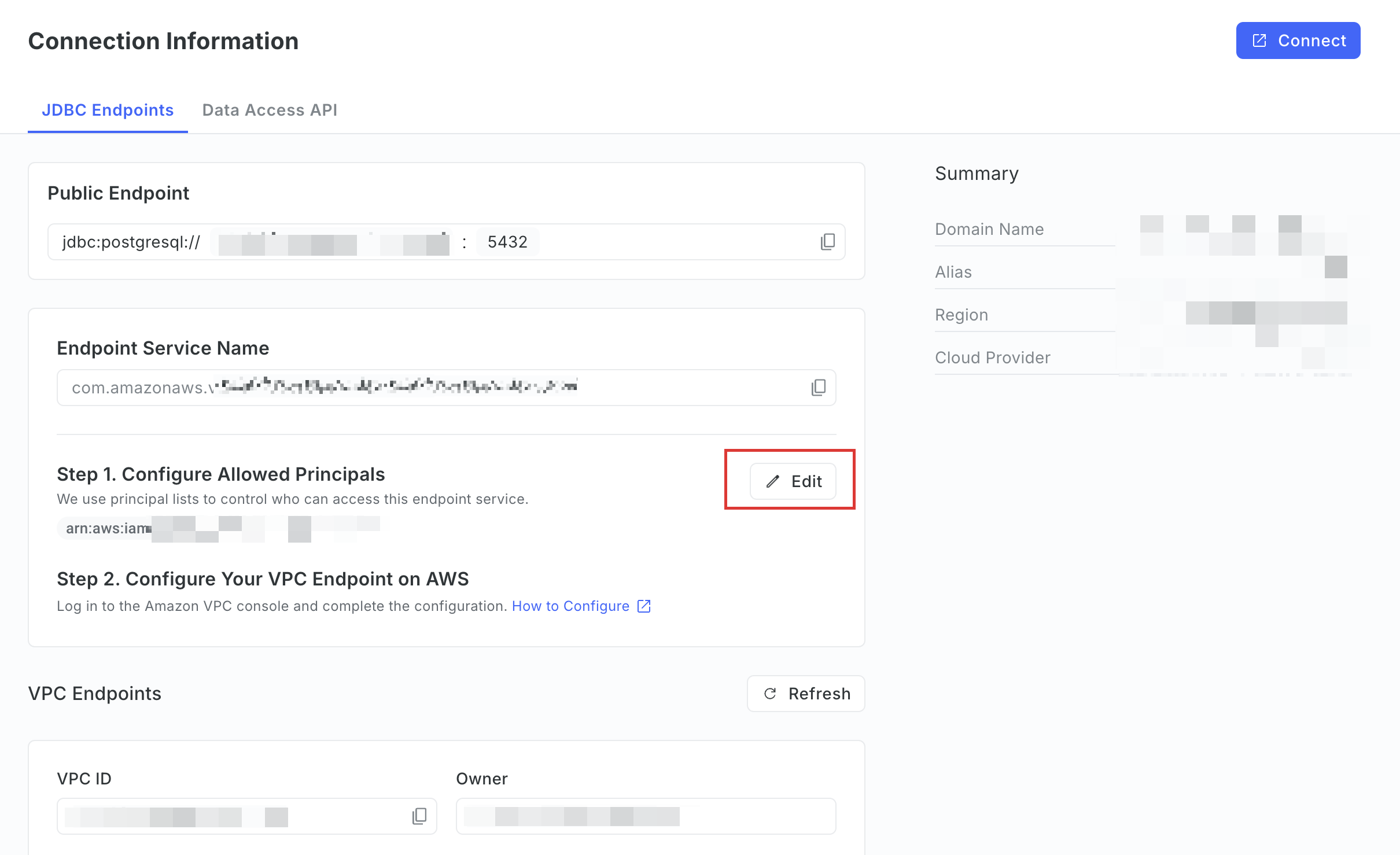
-
On the Allow Principals page, enter the Amazon Resource Names (ARNs) of the AWS principals you want to grant access to the endpoint service, then click Save.
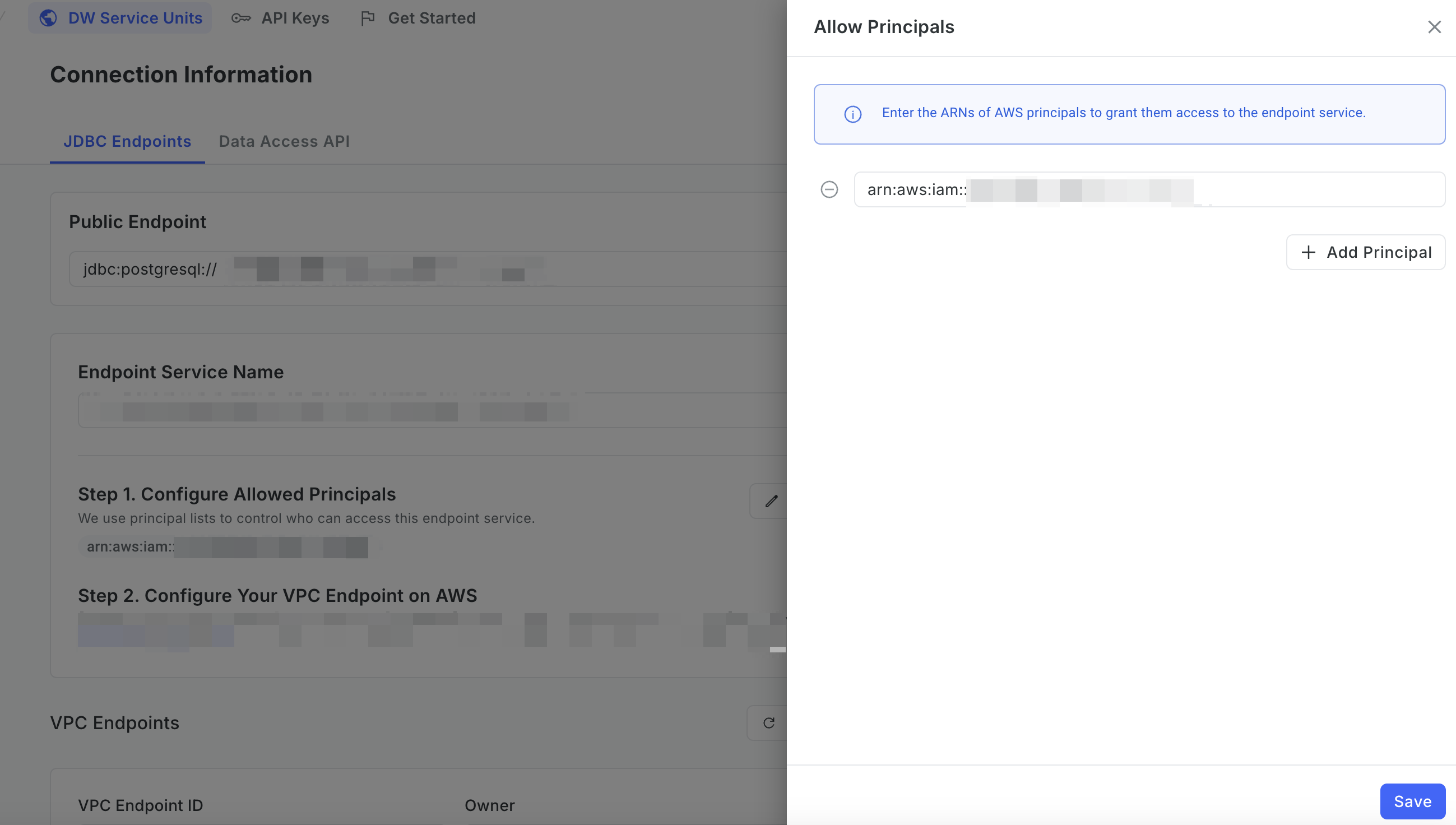 info
infoYou can set the ARN to * to allow all AWS principals to access the endpoint service. However, for security purposes, we recommend that you restrict access to a specific list of allowed principals.
The allowed principals list can be empty. If the list is empty:
-
The endpoint service will not be usable for creating new VPC endpoints on AWS as long as the allowed principals list remains empty on the Relyt side.
-
Existing VPC endpoints will remain unaffected and function as usual for the principals already configured.
-
-
Copy the value of the Endpoint Service Name for later use.
Step 2. Configure your VPC endpoint on AWS
-
Sign in to your Amazon VPC console.
ImportantEnsure that you VPC is in the same region as the DW service unit. Otherwise, the private link cannot be established.
-
In the left sidebar, choose Virtual private cloud > Endpoints.
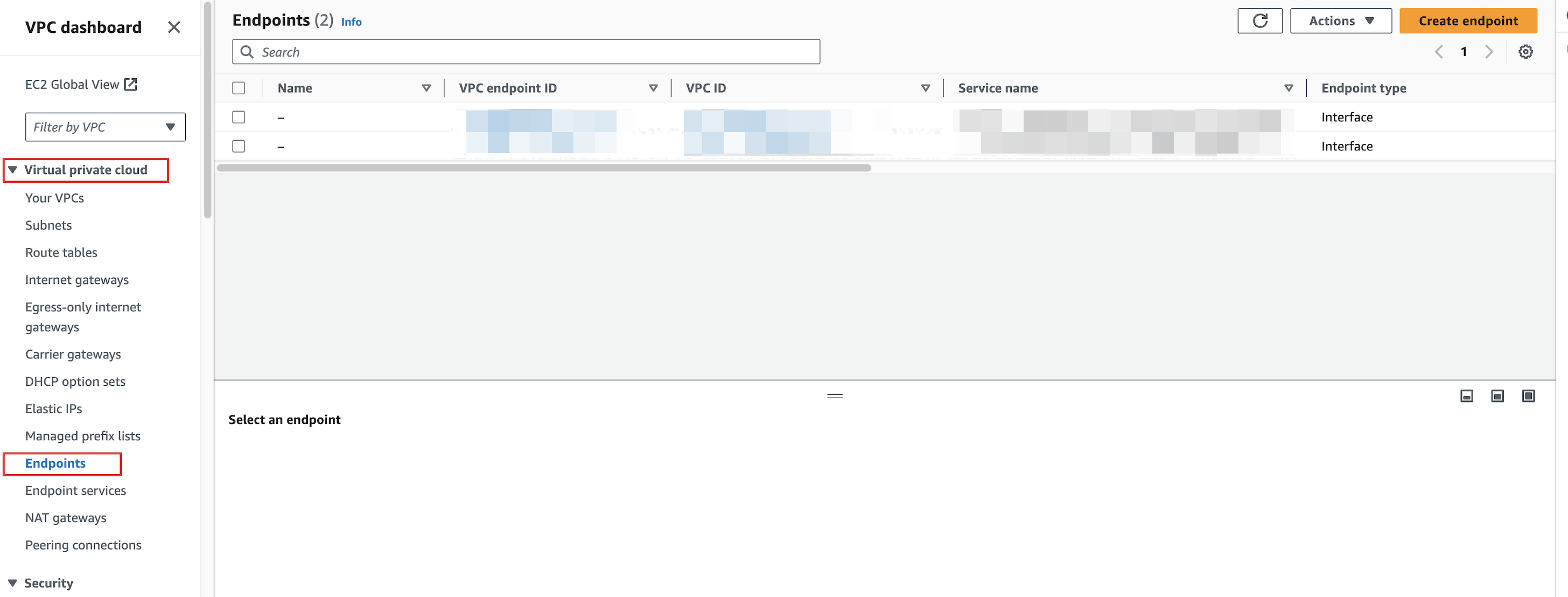
-
On the right corner of the Endpoints page, click Create endpoint.
-
In the Endpoint settings section, set Service category to Other endpoint services.
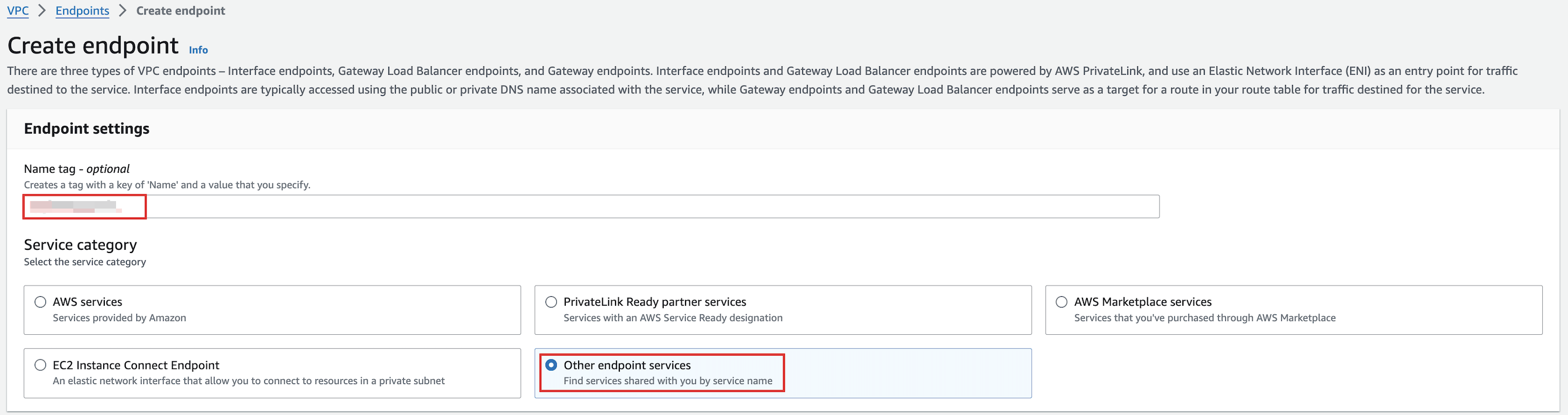
-
In the Service settings section, set Service name to the endpoint service name you obtained in Step 1, and click Verify service.
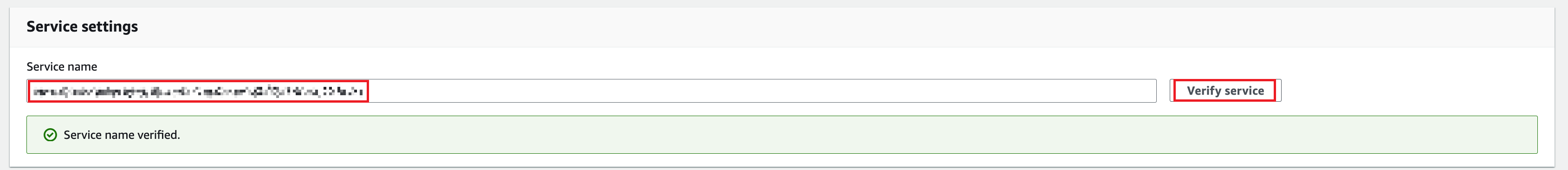
-
After the service is verified, in the VPC section, select the VPC you want to connect to your DW service unit.
-
In the Subnets section, configure the subnets for the VPC endpoint.
-
In the Security groups section, select the appropriate security groups.
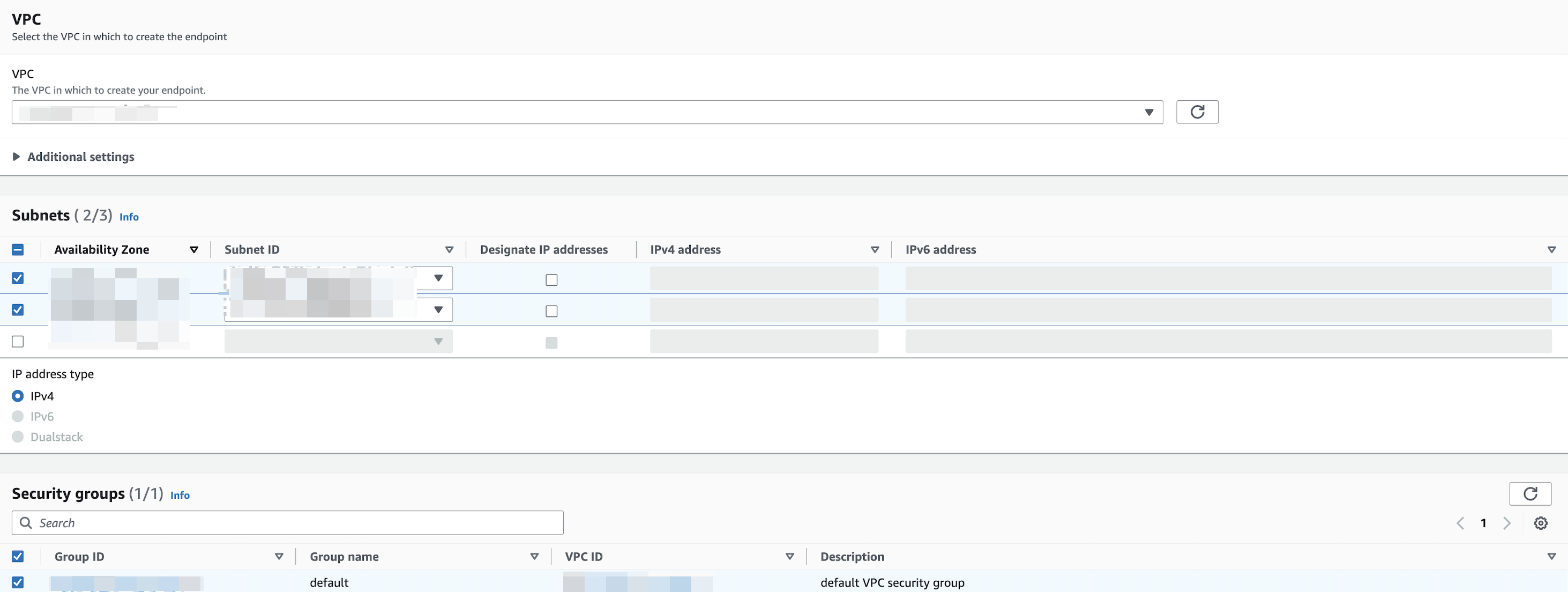
-
Click Create endpoint.
-
Wait for the endpoint status to change to Available.
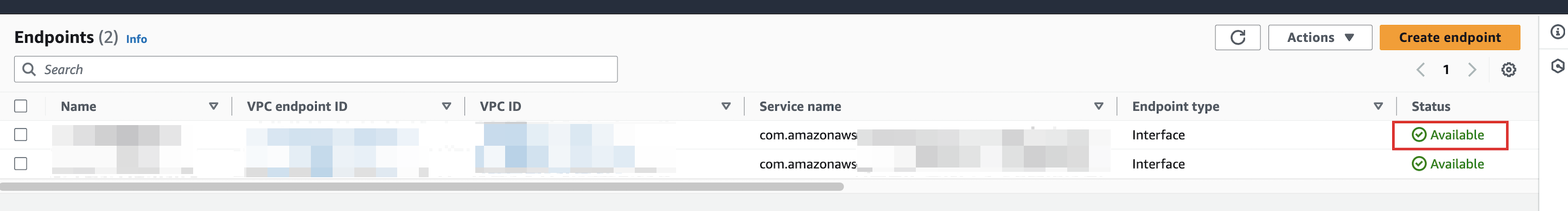
Step 3. Refresh your VPC endpoints on Relyt
Go back to your Relyt console, and refresh your VPC endpoint list.
-
If this is your first VPC endpoint in the DW service unit, click the Refresh button under the No VPC Endpoints Found message.
-
If there are already connected VPCs, click the Refresh button in the VPC Endpoints section.
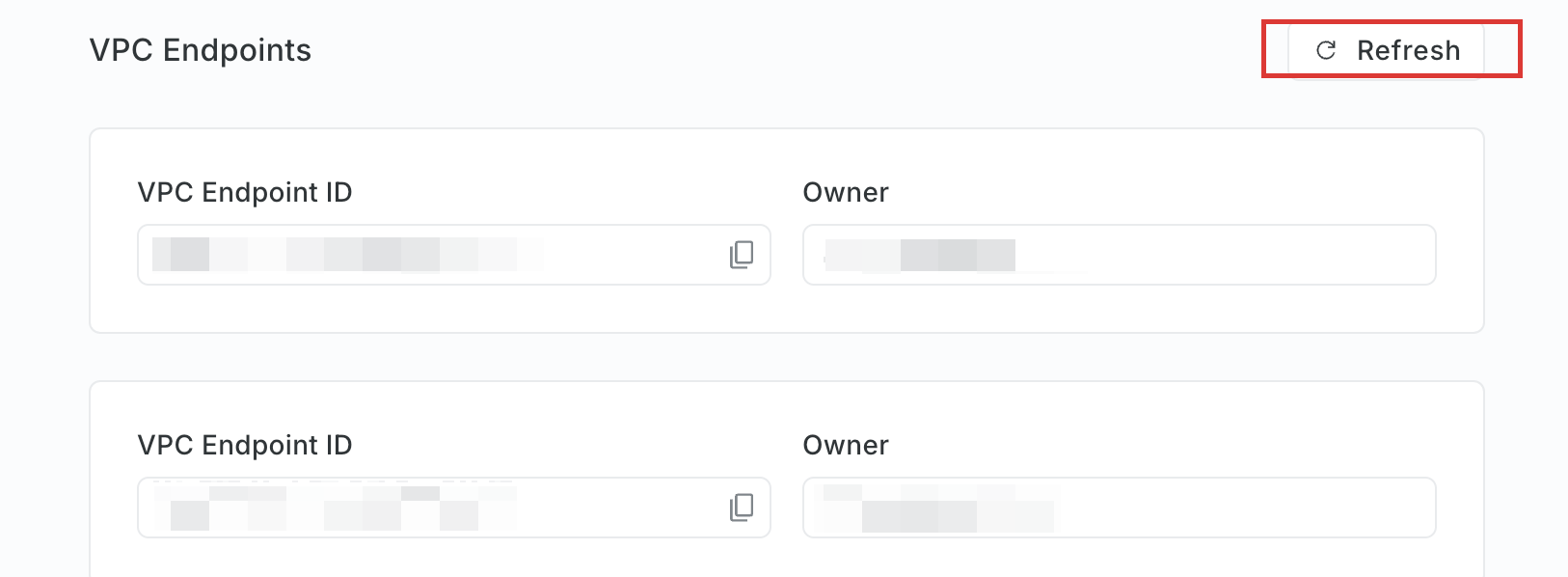
Now, you can view the ID and owner (AWS account ID of the creator) of the created VPC endpoint in the list.
Use a Terraform script to create a private link
This section describes how to run a Terraform script to automatically create a private link. To use the script, ensure you have obtained the API key that allows you to call Relyt Open API operations.
To obtain an API key, sign in to your Relyt console, choose API Keys from the top navigation bar, and click + API key to create one.
-
Download the latest Terraform script.
infoThis script creates two private links: one for Boto3 access and the other for JDBC tool access.
Following is a code snippet example from the module for creating private links. Configure the parameters according to your needs.
terraform {
required_providers {
relyt = {
source = "relytcloud/relyt"
}
}
}
provider "relyt" {
role = "SYSTEMADMIN"
}
resource "relyt_dwsu_privatelink" "pl_api" {
dwsu_id = "<dwsu_id>"
service_type = "data_api"
allow_principals = [
{ principal = "*" }
]
}
resource "relyt_dwsu_privatelink" "pl_db" {
dwsu_id = "<dwsu_id>"
service_type = "database"
allow_principals = [{ principal = "*" }]
}Parameter description:
Parameter Description sourceThe name of the Relyt plugin. It is fixed to relytcloud/relyt.roleThe system role of your Relyt cloud account. It is fixed to SYSTEMADMIN.dwsu_idThe ID of the DW service unit. service_typeThe service type. Possible values are data_apianddatabase. If you want to use Boto3 to connect through the private link, set it todata_api. If you want to use JDBC tools, set it todatabase.allow_principalsThe list of ARNs specifying the AWS principals permitted to access your AWS VPC through the private link. If you want to allow all AWS principals, set it to { principal = "*" }.
-
Open your terminal and navigate to the directory that contains the script.
cd <save_directory>Set
<save_directory>to the directory path where the script is saved. -
Run the following command to export the auth key.
export RELYT_AUTH_KEY="<api_key>"Replace
<api_key>with the API key you have obtained. -
Run the following command to initialize the Terraform working directory.
terraform init -
Run the following command to apply the module.
terraform apply --target=module.privatelink -
Enter
yesto confirm the operation.
After the private links are created, you can check them on the Connection Information page of the DW service unit.